DEVELOPMENT OF
AN AUTHENTICATION AND ACCESS CONTROL SOLUTION
FOR MOBILE DEVICES IN VIRTUAL PRODUCT AND
MANUFACTURING ENVIRONMENTS
Institute of
Graphic Interfaces (IGI), Korea,
2008.01-2008.06 (6 months).
► Introduction
In the
area of virtual product and manufacturing
environments, the protection of sensitive
information including technical data (e.g.
construction plans, simulation results) as
well as business related documents (e.g.
strategy papers, business plans, schedules,
minutes of executive meetings, internal
progress reports, proposals) is of outmost
importance for the commercial success of a
company, since quite a huge amount of
manpower and expertise had to be invested
into the creation of these data and these
documents contain a lot of valuable
information about future products or plans.
Two
foremost important security services for the
protection of such sensitive information are
user authentication and access control.
Motivated from the fact that, existing
authentication and access control approaches
are not quite applicable and flexible for
manufacturing environments, we are focusing
on design and develop a new security model
with key components are user authentication
and access control. Meanwhile, other
components are also provided including a
confidentiality module, a integrity module,
and a key management module.
► Scopes
We
have a very typical enterprise scenario
at hand. Companys information is stored
on its servers and we need to give
employees the access to information in
secure manner. Considering a simple
scenario, we will have an office and
site environment, where the employees
will be able to move from one place to
another in order to fulfill the
requirements of their jobs. They will
have PDA or other wireless devices
connected to the server through local
LAN. They will be able to view, update
or even delete information on the server
according to the access rights assigned
to them. Sample scenario is shown in
Fig. 1. Providing security in wireless
LANs has its own challenges. When we
talk about security, we have to protect
the data up to a point, where it becomes
infeasible for the attacker to attack.
The existing standard of 802.11 Wireless
LANs security is relatively new and has
many shortcomings, which we will discuss
in detail in Section 8. In this work, we
propose a Lightweight, Secure, Flexible
Access control (uSFA) framework for
mobile devices, which provides security
services like, authentication, access
control, key management, confidentiality
and integrity.
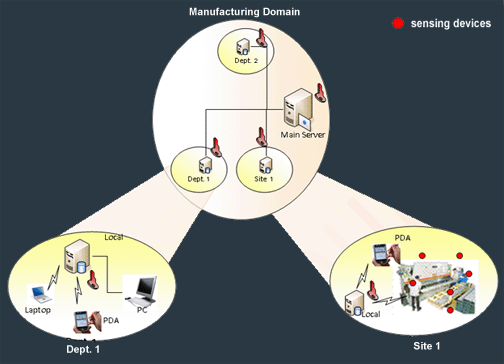
Fig.1 Sample Scenario
► Proposed
Framework
We aim
to provide a basic but dispensable
security services in a ubiquitous
manufacturing domain. Our proposed
system provides end-to-end, secure, and
flexible access from different types of
users to technical information. Our
security system involves authentication,
access control, confidentiality,
integrity, and key management scheme.
These components are constructed on the
foundation of a lightweight cryptography
library (encryption/decryption scheme).
The system architecture is depicted in
Fig. 2.
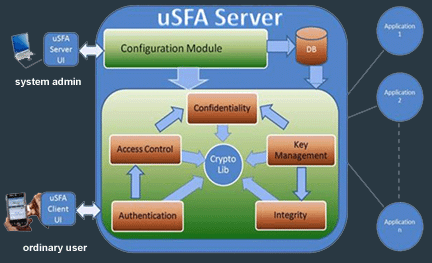
Fig. 2
The proposed
SFA
Framework
top