|

Currently, our team is working on
different security services for ubiquitous computing, including
authentication, access control, trust management, wireless sensor
network security, etc.
►Access
Control (by LX Hung)
more details
>>
[Summary]
Enterprise environments are
recognized as highly dynamic activity-center environments,
wherein granting resource access permissions to users
basically relies on what his is allowed to perform. Our
major focus is to propose a new approach which can reduce
the policy management cost, and flexibly support for user
activates.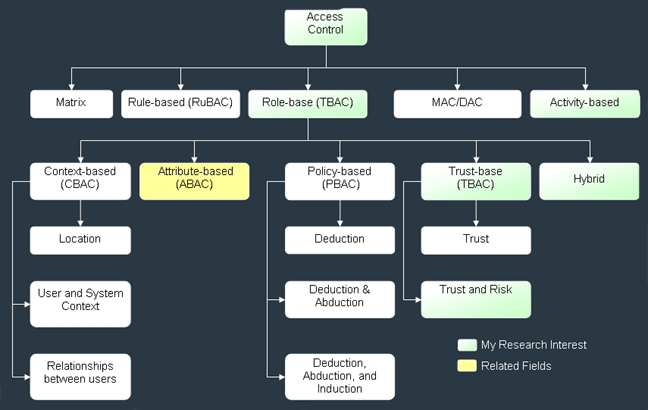
►Authentication
(by Hassan J.)
more details
>>
[Summary]
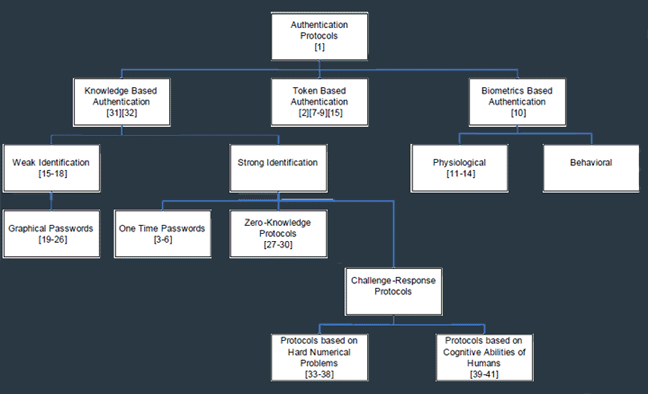
Our research on user authentication
is mainly focusing on providing a secure yet convenience way
for user to authenticate himself. An image-based approach
has been proposed. The proposed method can be applied on PC,
and hand-held devices
►Trust/Risk
Management (more details.)
[Summary]
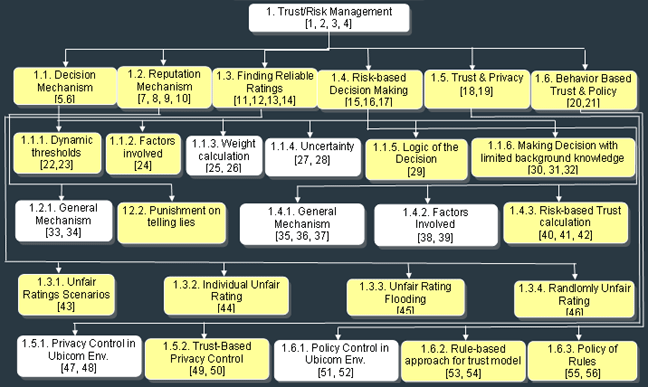
As ubiquitous computing environments
are highly changed with various unknown users, an trust
management model is necessary. We are working on different
aspects of trust and risk managements for ubicomp systems.
►
Key Management
(by Raazi & NTCanh)
more
details >>
[Summary]
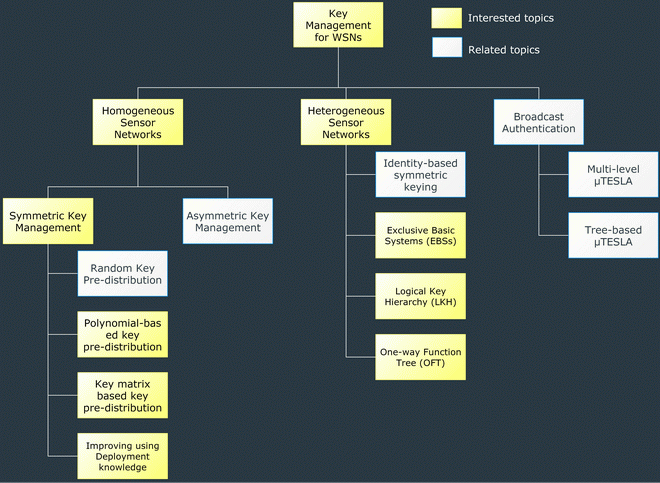
Key Management is the most important
and hard area in security. Our focus is to develop an
efficient key management scheme for mobile devices and
sensors.
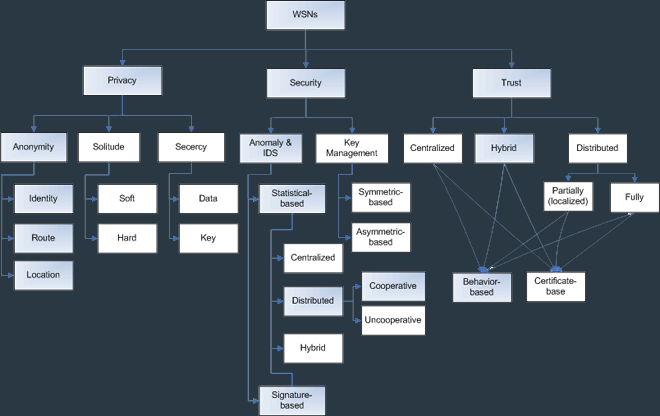
►
Wireless
Sensor Network security (by Riaz A. S.)
more details >>
[Summary]
Sensor networks are basic layer
for ubiquitous computing systems to sense and provide raw
context information. It relates to many security issues such
as privacy, integrity and confidentially of context
information.
top
|